The Security Experts for
— People, Technology, Organisation
Information Security Management : simple, strategic, sustainable
Our goals for you
Ensure operational capabilities in an emergency
Your advantages at a glance

Reduction of Efforts
Save up to 80% of the effort required to implement an ISMS by using tried and tested guidelines

Ready for use - immediately
Our implementation guides allow you to implement and use elements immediately in daily operations – no implementation process necessary

Provides logical transparency
Through our implementation, we ensure that employees are openly informed about the process

Direct ability for employees to take action
We ensure that your employees are immediately ready to act and are armed with all necessary knowledge and information

No more fear of the unknown
With our support, you and your employees will lose your fear of the unknown, and with that – gain control over your information security
Unser Ziel für Sie
Handlungsfähigkeit im Notfall sicherstellen
Ihre Vorteile auf einen Blick:

Reduktion der Aufwände
Sparen Sie durch vielfach erprobte Leitfäden bis zu 80% an Aufwänden, um eine ISMS-Implementierung operativ umzusetzen

Sofortige Nutzbarkeit
Durch unsere Implementierungsleitfäden können Sie die Elemente sofort in täglichen Betrieb einsetzen, kein Einführungsproiekt notwendig

Schafft verständliche Transparenz
Durch unsere Implementierung sorgen wir dafür, dass Mitarbeiter transparent über das Vorgehen informiert werden

Sofortige Nutzbarkeit
Wir sorgen dafür, dass Ihre Mitarbeiter direkt handlungsfähig sind und das notwendige Wissen vermittelt wird

Keine Angst vor Unbekannten
Durch unsere Implementierung sorgen wir dafür, dass Mitarbeiter transparent über das Vorgehen informiert werden
Our Guiding Principle
Secure Digitalisation in harmony with People, Technology, Organisation

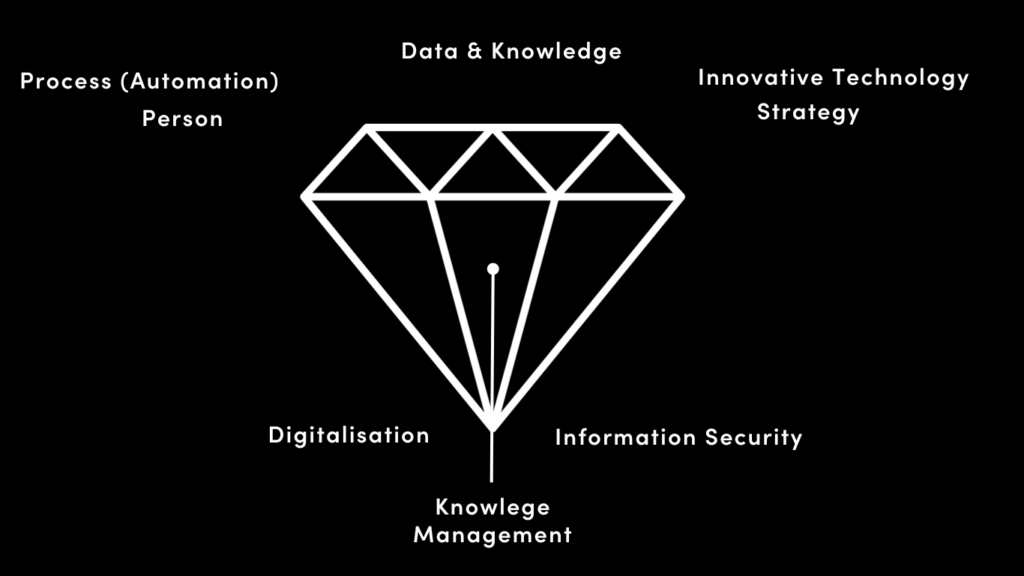
The three facets of digitization, knowledge management and information security define and secure the future for our customers.
For the meaningful and secure transformation of companies and organizations into a sustainable and successful future, we combine these topics and methods in a goal-oriented and effective manner. We listen carefully, understand you and your business. With us, everything becomes easier.
We start with an anamnesis workshop to determine the IT and Information Security Status. Based on the insights gained there, we define measures together.
We align possibilities and their uniqueness to maximize the benefits for you.
Unser Leitbild
— Sichere Digitalisierung im Dreiklang von Mensch, Technik, Organisation


Die drei Facetten Digitalisierung, Wissensmanagement und Informationssicherheit bestimmen und sichern die Zukunft unserer Kunden.
Für die sinnvolle und sichere Transformation von Unternehmen und Organisationen in eine
nachhaltige, erfolgreiche Zukunft kombinieren wir diese Themen und Methoden zielorientier und effektiv. Wir hören gut zu, verstehen Sie und Ihr Geschäft; mit uns wird alles einfacher.
Wir beginnen mit einem Anamnese Workshop zur Ermittlung des IT- und Informationssicherheitsstatus. Basierend auf den dort erlangten Erkenntnissen definieren wir gemeinsam Maßnahmen.
Wir bringen die Möglichkeiten und ihre Individualität in Einklang, um den maximalen Nutzen für Sie herauszuholen.
Do you know how your CYBER-SECURITY is doing?
Is your Information Security up to par?
Take a little time
For reporting and action directives in the context of cybersecurity
For a secure future

Anamnesis-Workshop
We will develop your strategy and your personal roadmap
Does IT Security seem like a mountain? You are facing it and feeling lost?
Where do we begin, and what way do we take to reach the summit?
Protect your company from digital threats! Book our Anamnesis Workshop on cybersecurity, gain transparency about your company’s situation, and receive clear actionable directives for the next steps in safeguarding against hacker attacks
For a Secure Future
In addition, we offer the following products and services:

Watchdog
Our watchdog provides transparency on all local computers/servers, network devices, patch levels in cloud services, configurations, security vulnerabilities etc. It is designed for the continuous monitoring of technical infrastructure.

Management System Development
The establishment of an efficient and sustainable Management System for Information Security and, if required, other Governance themes (ISO 27001, ISO 9001, etc.) rounds off our portfolio.

Data Protection as a Service
Get a secure concept tailored to the requirements of GDPR (DSVGO) and other IT compliance regulations. Book your external data protection officer here.
Gain transparency and security with us!
Security as a Service
Security-as-a-Service (SECaaS) is our answer for an innovative support service in IT security. Companies can book individual services as needed. "Everything is straightforward and expandable according to your own needs, and available as a subscription model."
The development, implementation, and optimization of digital business models is becoming increasingly essential for many companies as a key component of their competitive advantage. It requires new capabilities to ensure the security of complex IT infrastructure, which forms the foundation of all business areas.
Traditional IT security strategies often focus on processes and tools.
‘Modern IT security places people at the center of the action, aiming to optimize IT security awareness.’
In agile organizations, significant productivity improvements are possible. We operate entirely agile to provide these benefits to our customers in terms of speed and quality in our services.
With Security-as-a-Service (SECaaS), we offer our capabilities and best practices in pragmatic service packages as a monthly subscription. This allows companies to book individual IT security services with us or completely outsource their IT security needs.
At the beginning of each Security-as-a-Service engagement, we start with a personalized service onboarding. During this process, we discuss specific challenges with you, share activities already undertaken and document your individual expectations of us.
Subsequently, potential services from our service catalog are discussed and linked to your challenges to find solutions.
Key components of our service include emergency preparedness, complete overview, network security, data backup, updates, password + cryptography, system security, user management, security mindset, training, logging / time synchronization, infrastructure security, best practices, and compliance.
Regarding the Future of Hospitals Act (KHZG), we are a certified service provider and are happy to assist you with the application and implementation of your project.
Overview | How are you positioned?
Have all critical data and processes been identified, and have corresponding protection needs been addressed? What are the IT security requirements, which measures need to be prioritized for implementation, and how is the roadmap and responsibility defined for them?
Emergency Preparedness | What to Do When an Emergency Occurs?
Are emergencies identifiable, and do plans for emergency preparedness and response exist? Are responsibilities defined, and are those responsible capable of taking action? Do you and your employees know what to do in case of an emergency? Are the most important procedures known?
Evaluation of Compromises | Do You Monitor for Intrusions in Your System?
Are attempted attacks and compromised systems reliably detected?
Security Mindset, Training & Security Awareness is Key.
What priorities have been set regarding IT security, and what focus is being pursued? What is the budget for IT security and related training? Which measures have been successfully implemented? Is there a knowledge portal, regular teasers, and effectiveness assessments to actively promote security awareness among all stakeholders?
Planning and Implementation – Planning is Half the Battle.
Within the framework of a risk analysis, identified measures are planned, and we support their implementation and execution.
Network Security
What processes and measures are in place to support network security? How are anomalies detected, communicated, and addressed?
Patch Management
Updates are crucial and require proper attention.
What processes are in place for software maintenance and updates?
Data Backup – No Backup, No Sympathy
Are backups secure from deletion and manipulation over the network? Is restoration regularly tested?
Password + Cryptography | “123456” is Not a Password
What policies exist for passwords, (privileged) user accounts, 2-factor authentication, encryption (e.g., mobile devices)? How are these policies enforced?
System Security – Be Tough
What methodologies are used to harden systems?
User Management | Not Everyone Should See Everything
How is user management implemented, and what hierarchies, protective mechanisms, and processes are actively in use?
Logging / Time Synchronization
For investigating security incidents, seamless and accurate recording of log files is crucial. What methodologies and processes are in place for this purpose?
Infrastructure Security | EKG of the Infrastructure
Is there adequate protection for your IT systems against fundamental threats? How is appropriate access control ensured?
Compliance with Legal / Normative Requirements | §§§
Have the requirements of regulations such as the IT Security Act 2.0, BSI Basic Protection (BSIG §8a), ISO/IEC 2700x, Norm 62443, TISAX, KRITIS requirements, or B3S been fulfilled?
Implementation and Establishment of an ISMS
We support the implementation and establishment of an Information Security Management System (ISMS) following standards like ISO 27001.
Setting Up Security Monitoring | Knowing What’s Going On – Around the Clock
The implemented measures are integrated into monitoring to promptly inform stakeholders about incidents and report accordingly.
Support – You’re Not Alone, We’re Here for You
We, as service providers, plan and support the ongoing operation and necessary adjustments.
During the Service Onboarding/Anamnesis Workshop, we will establish the framework for your IT security, either in person where possible or via video conferencing if necessary. Essential requirements and priorities will be determined to ensure the success of our services and your IT security to the best possible extent. Additionally, we will discuss your wishes, challenges, and needs for a successful collaboration, all of which will be integrated into the service.
Our SECaaS team operates in an agile and digitally-oriented manner, allowing us to deliver high-quality service and work pragmatically with our clients.
In our service delivery, we utilize an NPS (Net Promoter Score) scoring system. This enables us to systematically understand your expectations and provide necessary suggestions for improvement.
If our service does not meet your expectations, we are willing to end the collaboration without any additional consequences for both parties and without harm. Through our transparent approach, we emphasize that there are no hidden costs involved. When you engage with us, you are booking your individual service package, and we will deliver the promised results.
Contact us!
You would like to learn more about Security as a Service?
Leave your email and we will contact you
SECaaS – Security as a Service
XaaS Enterprise GmbH
Sebastian-Kneipp-Straße 41
60439 Frankfurt
Copyright 2023 Theumert Consulting GmbH
All rights reserved.




